(Initial Submit) |
No edit summary |
||
| (6 intermediate revisions by the same user not shown) | |||
| Line 7: | Line 7: | ||
** Have configured VLANs and 802.1q trunking | ** Have configured VLANs and 802.1q trunking | ||
* Have a RADIUS server to point to (I do have a guide on how to setup [[Setup FreeRADIUS for 802.1x PEAP/MSCHAPv2 Auth against OpenLDAP|FreeRADIUS+LDAP]] if you need to set one up) | * Have a RADIUS server to point to (I do have a guide on how to setup [[Setup FreeRADIUS for 802.1x PEAP/MSCHAPv2 Auth against OpenLDAP|FreeRADIUS+LDAP]] if you need to set one up) | ||
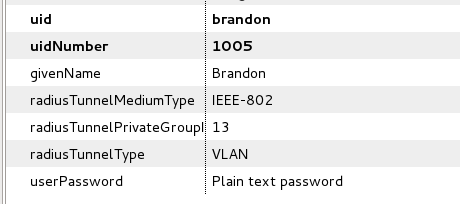
** In my case, with LDAP, your user looks something like this: | |||
[[file:Ldap-radius.png]] | |||
* Have your wired clients setup and able to do EAPoL | * Have your wired clients setup and able to do EAPoL | ||
| Line 30: | Line 32: | ||
! | ! | ||
! | ! | ||
interface FastEthernet0/ | interface FastEthernet0/1 | ||
switchport access vlan 999 | switchport access vlan 999 | ||
switchport mode access | switchport mode access | ||
| Line 36: | Line 38: | ||
dot1x pae authenticator | dot1x pae authenticator | ||
dot1x port-control auto | dot1x port-control auto | ||
! | ! | ||
radius-server host 10.0.3.2 auth-port 1812 acct-port 1813 key testing1234 | radius-server host 10.0.3.2 auth-port 1812 acct-port 1813 key testing1234 | ||
</syntaxhighlight> | </syntaxhighlight> | ||
* Thats pretty much about it. | |||
=== Things to note about the code === | |||
* Line 5: This is what enables the switch to change the VLAN to what is given by the RADIUS server. Without this, it just won't change the VLAN, and will put it in the access VLAN configured on the port, once authentication is successful. | |||
* Line 7: This actually enables 802.1x on the switch. One thing to note here is that 'port-control force-authorized' is the default on all ports. This way when you enable it, none of the ports go offline. | |||
* Line 11: You don't _have_ to configure an access VLAN here, but this is what it falls back to is RADIUS doesn't return anything. | |||
* Line 12: Before the 'dot1x' commands show up below, the port is required to be in access mode. You cannot have 802.1x on a trunking port. | |||
* Line 13: Not required, but allows machines on the network via the MAC address that do not have a 802.1x supplicant. The MAC just needs to be in your RADIUS server, with a password of the same MAC. | |||
* Line 14: Needed on newer switches. I found I didn't need it on the 2950's. This actually cause myself and another to not get 802.1x working on the 3750/2960 until I happened to come across it. This is not covered in the CCNP SWITCH Guide (although it is needed). | |||
* Line 15: This actually enables the authentication on the port. There are two other modes, but they aren't helpful to having the port authenticate. | |||
* Line 17: Radius server line, you can have multiple lines for different servers. Depending on the switch, the default ports could be in the 1600 range, so you may need to specify the port numbers here. The password goes after the 'key' term. | |||
== Resources Used == | |||
* [http://www.amazon.com/SWITCH-642-813-Official-Certification-Guide/dp/1587202433/ref=sr_1_1?ie=UTF8&qid=1348889727&sr=8-1&keywords=CCNP+Switch Cisco Official 642-813 (CCNP SWITCH) Certification Guide] | |||
* http://www.cisco.com/en/US/docs/switches/lan/catalyst3750/software/release/12.2_55_se/configuration/guide/sw8021x.html#wp1289244 - VLAN Assignment (3750) | |||
* http://www.cisco.com/en/US/docs/switches/lan/catalyst3750/software/release/12.2_55_se/configuration/guide/sw8021x.html#wp1025133 - 802.1x Configuration (3750) | |||
== Fin == | |||
I am available on IRC if you have any questions or comments; irc.freenode.net, my Nickname is Sedorox. I am usually in the #cisco channel, as well as others. | |||
Latest revision as of 03:57, 29 September 2012
Intro
There are many different guides out there on how to setup Cisco Switches to do 802.1x, or EAPoL. This is actually a part of the Cisco CCNP SWITCH exam. Generally, it's easy. Especially either reading the SWITCH Certification Guide, or reading over Cisco's website. The main thing I wanted to expand on while going through the SWITCH exam, was to expand 802.1x authentication into also assigning VLANs depending on what the RADIUS server returned for a specific user. When I read up on this, it was mostly "It just works(c)(tm)(r)", but it didn't for me. So, here's my documentation of how I got it to work. I'll dump the code in, then the things that need a bit more explaining, I'll explain below.
What does this page assume?
- You have basic Cisco IOS knowledge
- Have setup basic management connectivity (i.e. your switch can reach your RADIUS server)
- Have configured VLANs and 802.1q trunking
- Have a RADIUS server to point to (I do have a guide on how to setup FreeRADIUS+LDAP if you need to set one up)
- In my case, with LDAP, your user looks something like this:
- Have your wired clients setup and able to do EAPoL
My Testing Environment
- Several catalyst switch models
- 2950T-24
- 2950G-48
- 3550-24-PWR
- 3750-48-PS
- FreeRADIUS setup to refer to LDAP, so thats how I'll be referring to accounts and what they contain.
- Windows 7
- Mac OS X Mountain Lion
The Code
aaa new-model
!
!
aaa authentication dot1x default group radius
aaa authorization network default group radius
!
dot1x system-auth-control
!
!
interface FastEthernet0/1
switchport access vlan 999
switchport mode access
dot1x mac-auth-bypass
dot1x pae authenticator
dot1x port-control auto
!
radius-server host 10.0.3.2 auth-port 1812 acct-port 1813 key testing1234- Thats pretty much about it.
Things to note about the code
- Line 5: This is what enables the switch to change the VLAN to what is given by the RADIUS server. Without this, it just won't change the VLAN, and will put it in the access VLAN configured on the port, once authentication is successful.
- Line 7: This actually enables 802.1x on the switch. One thing to note here is that 'port-control force-authorized' is the default on all ports. This way when you enable it, none of the ports go offline.
- Line 11: You don't _have_ to configure an access VLAN here, but this is what it falls back to is RADIUS doesn't return anything.
- Line 12: Before the 'dot1x' commands show up below, the port is required to be in access mode. You cannot have 802.1x on a trunking port.
- Line 13: Not required, but allows machines on the network via the MAC address that do not have a 802.1x supplicant. The MAC just needs to be in your RADIUS server, with a password of the same MAC.
- Line 14: Needed on newer switches. I found I didn't need it on the 2950's. This actually cause myself and another to not get 802.1x working on the 3750/2960 until I happened to come across it. This is not covered in the CCNP SWITCH Guide (although it is needed).
- Line 15: This actually enables the authentication on the port. There are two other modes, but they aren't helpful to having the port authenticate.
- Line 17: Radius server line, you can have multiple lines for different servers. Depending on the switch, the default ports could be in the 1600 range, so you may need to specify the port numbers here. The password goes after the 'key' term.
Resources Used
- Cisco Official 642-813 (CCNP SWITCH) Certification Guide
- http://www.cisco.com/en/US/docs/switches/lan/catalyst3750/software/release/12.2_55_se/configuration/guide/sw8021x.html#wp1289244 - VLAN Assignment (3750)
- http://www.cisco.com/en/US/docs/switches/lan/catalyst3750/software/release/12.2_55_se/configuration/guide/sw8021x.html#wp1025133 - 802.1x Configuration (3750)
Fin
I am available on IRC if you have any questions or comments; irc.freenode.net, my Nickname is Sedorox. I am usually in the #cisco channel, as well as others.